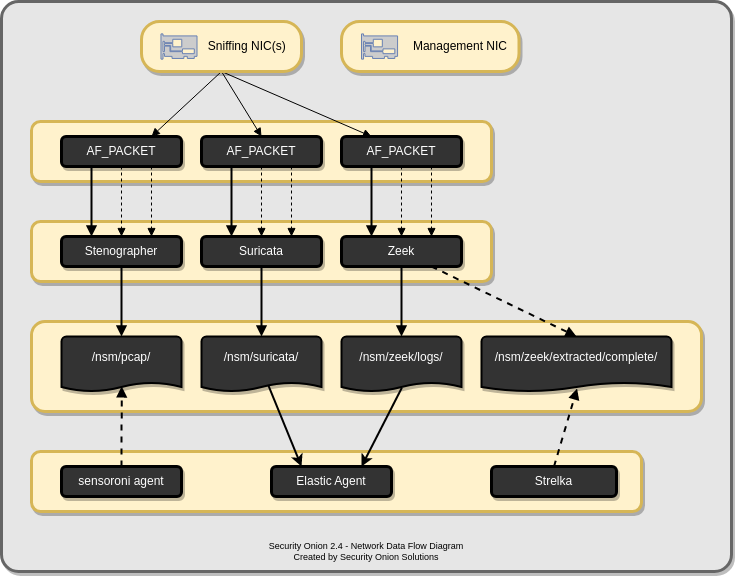
Network Visibility
When you log into Security Onion Console (SOC), you may see alerts from Suricata or Intrusion Detection Honeypot, protocol metadata logs from Zeek or Suricata, file analysis logs from Strelka, or full packet capture from Stenographer or Suricata. How is that data generated and stored? This section covers the various processes that Security Onion uses to analyze and log network traffic.